4 min read
How to Avoid Getting Hooked by Phishing
This blog post is in partnership with LMG Security. With professional hackers and cybersecurity criminals posing a constant threat to law firms...
We've crafted solutions tailored to your firm
The world of insurance for law firms can be confusing, and difficult to navigate. We've created this glossary because these common insurance terms should be easy to understand.
6 min read
 LMG Security
:
Updated on June 7, 2023 | Posted on February 14, 2023
LMG Security
:
Updated on June 7, 2023 | Posted on February 14, 2023

How do cybercriminals break into a law firm? It can be startlingly quick and easy. We’re going to take you through the step-by-step process of how hackers get into your computer and environment with very little time and resources, then expand their access to take over your entire network and even deploy ransomware. Along the way, we’ll also share prevention strategies to minimize the damage.
CISA has identified the top five ways attackers gain initial access to a network as:
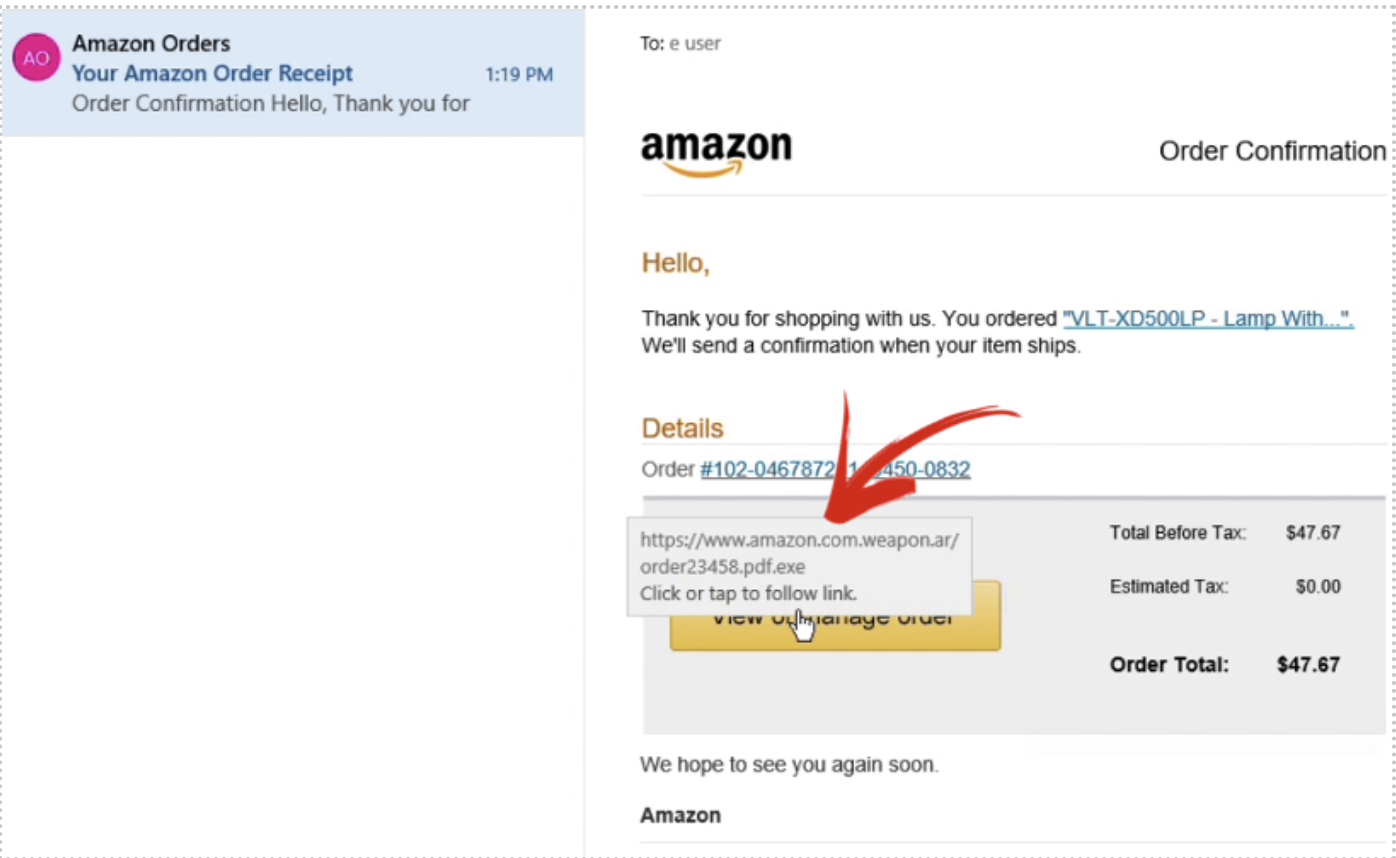
One of the most popular initial access attacks is phishing. The 2022 Verizon Data Breach Investigation Report found that 82% of breaches involved a human element — e.g. social engineering — and over 60% of those attacks were a result of phishing. Hackers can create a simple malware program that opens up a backdoor to your network in as little as 30 minutes. Then it’s a simple matter of creating a phishing email.
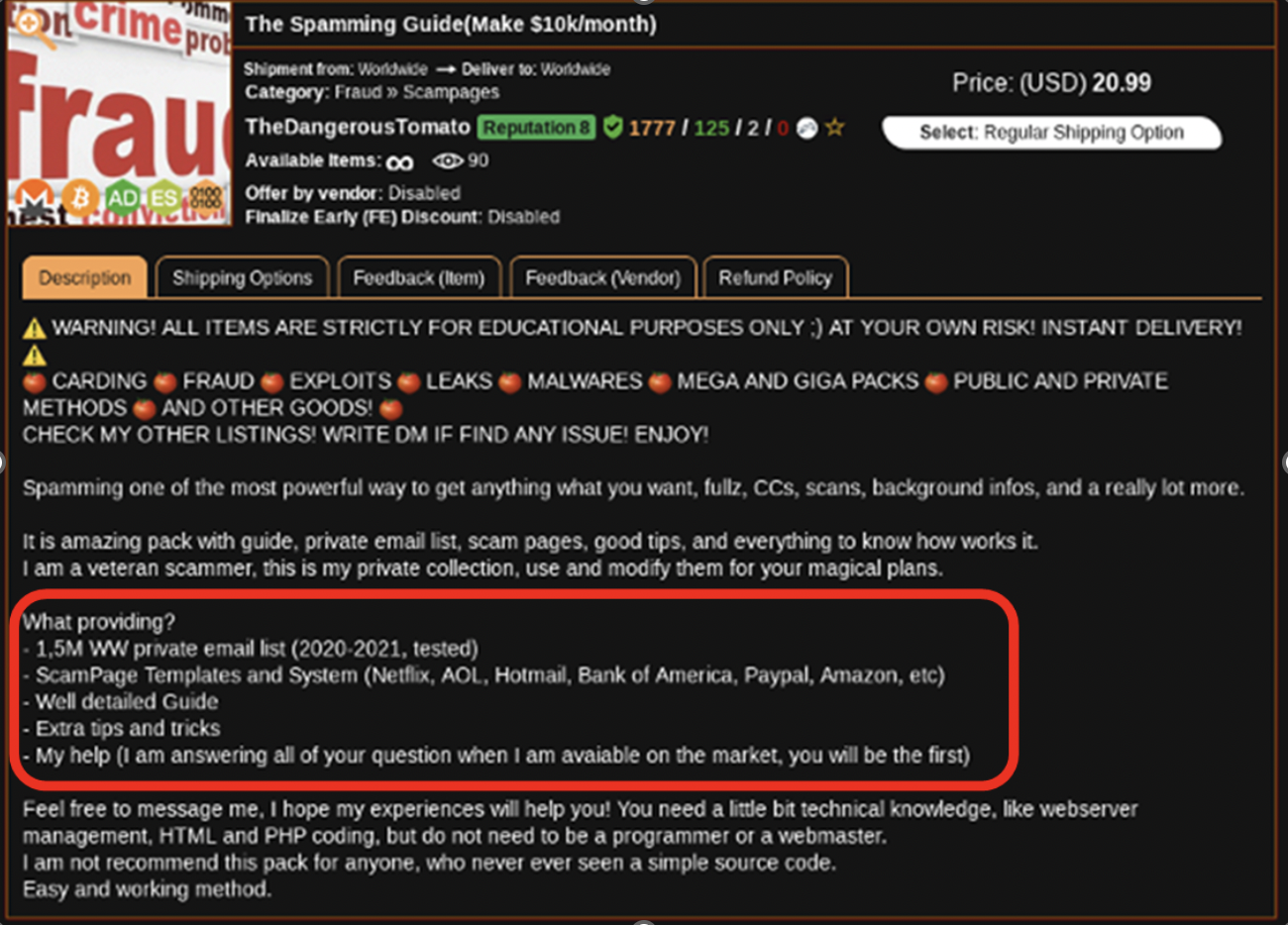
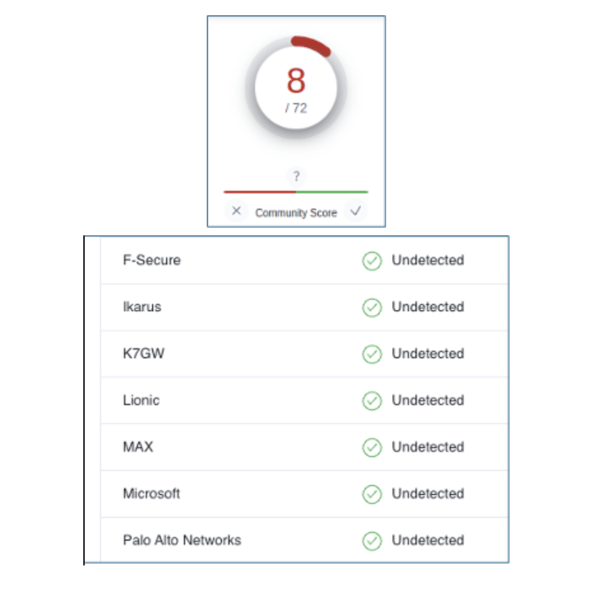
However, today’s criminals don’t even need to put in that much effort. It’s easy and inexpensive to buy a phishing and malware-as-a-service kit that comes with everything from the phishing email to the fake payment screens that steal your information. As you can see in the screenshot from a dark web marketplace below, hackers can buy an inexpensive kit – including several choices of spoofed page templates for major brands – to quickly start a malware campaign.
2. Internal Reconnaissance.
Once inside, Evil Tom leverages Erik L. User’s access to search for file shares and web servers on the local network by using a port scanning tool. One of the servers that pops up on his radar is the administrative web interface of a printer, in addition to multiple file servers. This gives Evil Tom information that he will use to expand his access.
How can you prevent this from happening?
A. Network Segmentation
Regardless of how hackers get into your computer, network segmentation is a basic yet very effective way to limit the amount of your network a hacker can access if they enter your environment. Read 7 Network Segmentation Best Practices That Stop Malware’s Lateral Spread for more information.
B. Use network detection and response tools. NDR tools like Extrahop, port scan detection tools like PortSentry, and IDS tools such as Zeke, Snort, or Suricata can detect and alert you when an attacker is scanning your network. But you also have to actively monitor these tools, otherwise you will miss the alerts. If you have limited staff, consider EDR/XDR solutions that can automatically block the hacker’s access when they detect these scanning activities.
3. Printer Hacking! Printers are frequently a steppingstone for hackers and overlooked by defenders. In this case, Evil Tom was able to browse the printer’s web application and access many of its configuration settings without any authentication. The default setting for many printers is to allow access to its web application without a password. For printers with a password, many users forget to change the default password which is available via a quick Google search.
This smart printer can scan documents to users’ email addresses. To do this, it is configured with a domain user account that is used to query the local LDAP server and obtain information about user email addresses.
Evil Tom decides to capture the printer’s domain credentials. To do this, he sets up a fake LDAP server—we’ll call this the Evil LDAP server. Then, he reconfigures the printer so that it attempts to query the Evil LDAP server for information, instead of the real one. At the same time, Evil Tom launches a network sniffing tool, Wireshark, which listens to the traffic sent to the Evil LDAP server.
When the printer attempts to query Evil LDAP server, the printer’s password is captured by Tom’s network sniffer. Voila! Evil Tom now has the printer’s domain credentials.
Next, Evil Tom uses an LDAP program to track all the network traffic when people sign in with their username and password and send it to his server.
How can you prevent this from happening?
Harden your system configuration to prevent hackers from gaining access:
4. The Hacker Expands Access. Evil Tom runs an automated program to determine where the printer has read/write access. He finds access to a file share containing backups. Searching the backups, he finds a configuration file buried deep within which contains a domain administrator password. Jackpot! This scenario is all too common: over the years, files containing passwords often accumulate in unexpected file shares, left by previous IT administrators or contractors that never cleaned things out.
Using the stolen administrator password, Evil Tom now has access to all of HackMe’s files including accounts, billing, financial details, and more.
How can you prevent this from happening?
A. Use the principle of least privilege. Only give each employee the exact amount of access they need to do their job. Regardless of how hackers get into your computer, if you can make it difficult for an attacker to access sensitive data, you can limit the damage. You can also manage this with role-based access permissions; restricting access can stop a hacker from expanding their privileges.
5. Takeover! Evil Tom uses RDP to remotely connect to the domain controller using the stolen administrator password. From there, he uses a tool to dump all credentials from the domain controller. For any encrypted passwords he uses an automated password cracking tool that makes billions of guesses in seconds to decrypt the information. Evil Tom now has full access to HackMe’s network and can login with administrative access to the entire organization and encrypt the whole network.
How can you prevent this from happening?
A. Deploy multifactor authentication. This can stop a hacker in their tracks. It’s not just for external servers; using MFA for internal administrator access could have stopped Evil Tom from connecting to HackMe’s domain controller and thwarted his takeover plans.
B. Conduct annual penetration tests. Penetration tests by ethical hackers are one of the best ways to find your weaknesses before a criminal can exploit them. You’ll get an accurate understanding of your risk and a list of issues and weaknesses that automated scans won’t detect. If HackMe had recently had a penetration test, the misconfigurations, missed patches, and cyber hygiene issues could have been caught and proactively corrected to detect the hacker and minimize the damage he caused in the network.
We hope you found this example of how hackers get into your computer and environment helpful! If you’d like to see the video of Evil Tom’s attack on HackMe, Inc., watch our 11-minute video of how hackers get into your computer or the full 1-hour on-demand webinar. Now that you know how a hacker can access your environment and some steps to prevent that access, we hope you will implement these cybersecurity tools and policies. Contact the LMG Security team if you need help.
At LMG, our singular focus is on providing outstanding cybersecurity consulting, technical testing, training, and incident response services. Our team of recognized cybersecurity experts have been covered on the Today Show and NBC News, as well as quoted in the New York Times, Wall Street Journal, and many other publications. In addition to online cybersecurity training, LMG Security provides world-class cybersecurity services to a diverse client base located around the United States and internationally.

4 min read
This blog post is in partnership with LMG Security. With professional hackers and cybersecurity criminals posing a constant threat to law firms...

3 min read
This blog post is in partnership with LMG Security. With professional hackers and cybersecurity criminals posing a constant threat to law firms big...
In today's connected world, mobile phones have become an integral part of our lives. They provide us with convenience, communication, and a wealth of...