In today's connected world, mobile phones have become an integral part of our lives. They provide us with convenience, communication, and a wealth of information at our fingertips. However, this increased connectivity comes with inherent security risks. As our reliance on mobile phones grows, so does the need to protect our personal and sensitive data from potential threats. To help you keep your organization safe, let’s dive into the current threat landscape, popular forms of mobile device deployment, and a checklist of mobile device security best practices.
The Mobile Threat Landscape
Why are we so concerned about mobile device security? Today’s smartphones are likely to be officially or unofficially used for work since almost ¾ of employees work remotely at least part of the time. In fact, one recent report found that 85% of employers require employees to install work apps (often an authentication app) on their personal devices. This report also found that 71% of employees store sensitive work passwords on their personal phones. So, regardless of whether your organization has a formal BYOD policy, it’s likely that your organization’s passwords and data can be found on employee phones and personal devices. That means one mobile device breach could compromise your security.
Common Mobile Device Policies & Risk Profiles
The major Uber breach in 2022 started from a contractor’s infected personal device and led to a full network takeover. It’s important that you consider which of the four common mobile device deployment policies is the best fit for your organization, as each approach offers varying levels of flexibility, control, security, and costs. Choosing the most suitable approach depends on factors such as your organization's security requirements, industry regulations, and employee needs. Here’s a brief overview of policy categories:
- BYOD (Bring Your Own Device). With a BYOD policy, employees use their personal mobile devices for work. BYOD is the least expensive approach for organizations as the employee provides and maintains their own device and plan, but it also has the highest security risks. Users may use risky apps or allow their children to play unsecured games on their devices. Some organizations add mobile device management (MDM) software to protect their data, but employees may object to employer oversight on their personal devices. However, BYOD is still a popular program since it is inexpensive, employees have the flexibility to use the phone of their choice, and employees can carry one device.
- CYOD (Choose Your Own Device). CYOD is a policy where employees are given the flexibility to choose a work phone from several pre-approved devices that meet specific security and compatibility criteria. This approach strikes a balance between BYOD and COPE, offering a controlled device environment while accommodating individual preferences. All properly managed corporate-owned device policies are lower risk than BYOD but also involve a much higher cost for devices, mobile plans, and management.
- COPE (Corporate-Owned, Personally Enabled). COPE involves providing employees with mobile devices that are owned and managed by the organization but allow limited personal use. The organization retains control over the device and can enforce security policies and restrictions. COPE offers a higher level of control and security compared to BYOD, as the organization has more oversight and can configure the devices to meet specific security standards. Employees can still use the devices for personal tasks within predefined boundaries.
- COBO (Corporate-Owned, Business-Only). COBO is a policy where the organization provides and manages mobile devices that are for work-related activities only, and personal use is strictly prohibited. Many employees can find this frustrating as they may need to carry, charge, and use two different phones. COBO offers the highest level of control and security with no mixing of personal and corporate data or applications. A COBO policy is one of the most important mobile device security best practices for highly regulated industries that require strict compliance and data protection policies.
How Are Criminals Breaking Into Your Device?
As criminals increasingly target mobile devices to gain access to the employer’s network, here’s an overview of the common attack methods:
- Text Phishing (aka “Smishing”). Smishing has a higher success rate than phishing, likely because caller ID is easy to spoof, and mobile phone screens are so small that it makes it harder to spot phishing websites. Since mobile phones often store sensitive information, attackers are increasingly using smishing attacks to access a larger network. In the image below, you can see how these attackers try to trick users into clicking the link and providing information such as PINs, MFA codes, or passwords.
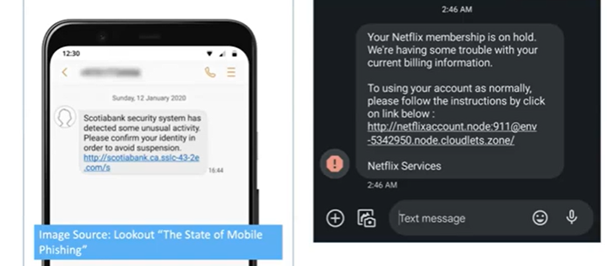 Image source: Lookout
Image source: Lookout
- Malicious Apps. Attackers are using malware loaders to inject malware into legitimate apps that initially pass security for the major app stores before they are caught and removed. These apps can use key loggers, turn on the camera and audio, obtain permissions to access almost everything on your phone, and more.
- Voice Phishing (aka “Vishing”). Criminals can easily spoof caller ID and use a voice-changing program to leave professional-sounding prerecorded messages to try to get you to enter a code or password to “secure your account.” This is a popular tactic to steal MFA codes or get you to provide personal information to a call center agent.
- MFA Bypass Attacks. According to Okta, MFA bypass attacks almost doubled in the first half of 2022. One-time passwords and codes are an attractive target for criminals as these are the easiest path for MFA bypass attacks. MFA bombing, a type of MFA fatigue attack, is an attack where the criminals send non-stop requests (sometimes late at night) until the victim clicks yes to authenticate or sends an MFA code. This tactic was used in the Uber breach to bypass MFA. They spammed the MFA message for an hour, then reached out over WhatsApp to the user claiming to be from Uber IT, and told the user he needed to accept the message to make it stop. This enabled the criminal to get into Uber’s network.
- SIM Swapping. Criminals can get fraudulent access to your phone by porting your number to their device in a SIM-swapping attack. In 2020, a hacker conducted a SIM-swapping attack through Twitter when they compromised the management dashboard and took over about 130 high-profile accounts. The attacker then ran a cryptocurrency scam from these well-known Twitter users and tricked some people into sending them money.
- QR code phishing. Attackers sometimes place stickers with malicious QR codes on a menu or ATM machine to trick people into completing a survey or downloading an app that steals information or infects them with malware. In one example, a QR code prompted a victim to download an app that gave the attacker full access permissions to the device, and they stole $20K from the victim’s bank account.
The best way to avoid these mobile device risks is to follow mobile device security best practices and upgrade to secure MFA such as biometrics, authentication apps, or hardware tokens, rather than text or email MFA codes that can be more easily intercepted. For more information on safer MFA, you can also watch our on-demand Beyond Passwords webinar.
Mobile Device Security Best Practices
Having a mobile security plan is crucial in today’s digital world. Ensure you incorporate these mobile device security best practices in your organization’s cybersecurity plans and policies:
- Implement device and access control.
- Deploy mobile device management software (MDM).
- Vet and limit apps on mobile devices.
- Deploy conditional access policies.
- Coordinate with remote workers that travel.
- Establish mobile phishing defenses.
- Require phishing-resistant MFA.
- Disable weak MFA such as phone calls, SMS-based authentication, etc.
- Conduct user awareness training which includes SMS phishing, QR code phishing, and other device security issues. For more details, read our checklist for effective phishing training.
- Encourage safe user habits.
- Opt out of personal data collection on mobile devices.
- Ensure web traffic is encrypted when surfing.
- Use a virtual private network (VPN) for browsing.
- Implement software security.
- Use reputable antivirus/antimalware software.
- Keep your operating system and apps up to date.
- Don’t jailbreak or root mobile devices.
- Consider mobile supply chain security.
- Routinely conduct data & asset inventories.
- Know your suppliers (including app providers & carriers).
- Include suppliers in response & security planning.
- Implement physical security measures.
- Set a strong passcode or use biometric authentication on devices.
- Ensure device-level encryption is on.
- Backup data on mobile devices.
- Maintain a clear process for reporting lost/stolen devices.
- Enable remote wipes so that you can remotely erase all data in case a device is lost or stolen.
We hope you found this information helpful. Contact us if you need help developing security policies or implementing cybersecurity solutions. Our expert team is ready to help!
This blog is distributed with the permission of LMG Security.
 LMG Security
:
Posted on June 13, 2023
LMG Security
:
Posted on June 13, 2023
 Image source: Lookout
Image source: Lookout

